Activity: Decrypt an Encrypted Message
Activity Overview
In this lab, I completed a series of tasks to decrypt an encrypted file, demonstrating the critical role of encryption in securing data in use, at rest, and in transit. Using my Linux skills, I uncovered clues needed to decode a classical cipher, restore a file, and reveal a hidden message, showcasing practical encryption techniques and their importance in safeguarding information.
Tasks
- Listed the contents of a directory.
- Read and analyzed the contents of files.
- Used Linux commands to decode a classical cipher back to plaintext.
- Decrypted an encrypted file and restored it to its original state.
Scenario
In this scenario, all files in my home directory were encrypted, requiring me to use Linux commands to break a Caesar cipher and decrypt the files to reveal hidden messages.
To complete this task, I first explored the contents of the home directory and read the contents of a file. Next, I discovered a hidden file and successfully decrypted the Caesar cipher within it. Finally, I decrypted the encrypted data file to recover the data and reveal the hidden message.
Task 1: Read the Contents of a File
The lab starts in my home directory, /home/analyst, as the current working directory. In this task, I explored the directory contents and read a file to obtain further instructions.
I used the ls command to list the files in the current directory. This revealed two files, Q1.encrypted and README.txt, as well as a subdirectory, caesar.
To proceed, I used the cat command to read the contents of the README.txt file:
The output provided a crucial message:
"Hello, All of your data has been encrypted. To recover your data, you will need to solve a cipher. To get started, look for a hidden file in the caesar subdirectory."
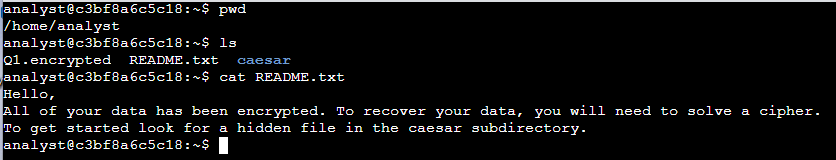
The message advised that the caesar subdirectory contains a hidden file, guiding the next step of the decryption process.
Task 2: Find a Hidden File
I needed to locate a hidden file in my home directory and decrypt the Caesar cipher it contained, enabling me to proceed with the next task.
First, I navigated to the caesar subdirectory using the cd command. Then, I used the ls -a command to list all files, including hidden ones, and found the hidden file .leftShift3.
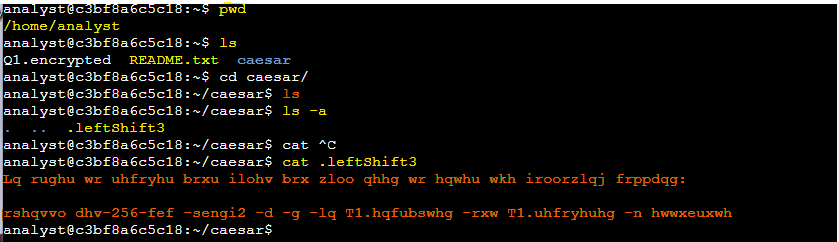
Hidden files in Linux are identified by names starting with a period (.). To decrypt the hidden file, I read its contents using the cat command. The message appeared scrambled, as it was encrypted using a Caesar cipher, with each letter shifted three positions to the left. To decrypt it, I used the tr command:
cat .leftShift3 | tr "d-za-cD-ZA-C" "a-zA-Z"
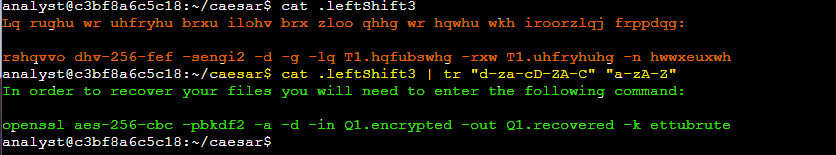
tr command translated each letter back to its original position, allowing me to decrypt the cipher and continue to the next step. I returned to the home directory to prepare for the next task.
Task 3: Decrypt a File
After solving the Caesar cipher, I used the command revealed in the .leftShift3 file to decrypt the Q1.encrypted file and recover the hidden message. I executed the following command to decrypt the file:
openssl aes-256-cbc -pbkdf2 -a -d -in Q1.encrypted -out Q1.recovered -k ettubrute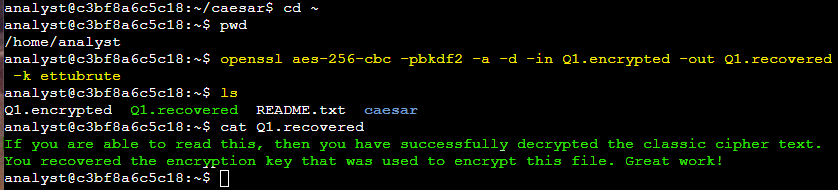
This command used openssl to reverse the encryption with the AES-256-CBC cipher. The -pbkdf2 option added security to the key, -a specified the output encoding, and -d indicated decryption. The -in and -out flags were used to specify the input and output files, while -k indicated the password, which in this case was ettubrute.
After decrypting the file, I used the ls command to list the contents of the directory. The newly decrypted file, Q1.recovered, was displayed. The output revealed:
"If you are able to read this, then you have successfully decrypted the classic cipher text. You recovered the encryption key that was used to encrypt this file. Great work!"
I successfully decrypted the Q1.encrypted file, recovered the data, and read the hidden message.
Conclusion
In this lab, I gained practical experience using Linux Bash commands to:
- List hidden files,
- Decrypt a Caesar cipher, and
- Decrypt an encrypted file.
This lab provided hands-on knowledge in understanding encryption and decryption techniques—an essential skill for security tasks.