Activity: Create Hash Values
Introduction
Hash functions are used to uniquely identify the contents of a file so that we can check whether it has been modified. This code provides a unique identifier known as a hash value or digest.
In this lab, I created and evaluated the hash values for two files. I used Linux commands to calculate the hash of each file and observed any differences in the hashes produced. I then determined whether the files were the same or different.
Scenario
In this scenario, I investigated whether two files were identical or different.
Here’s how I completed this task: First, I displayed the contents of the two files and created hashes for each file. Next, I examined the hashes and compared them.
Tasks:
- Listed the contents of the home directory.
- Compared the plain text of the two files presented for hashing.
- Computed the
sha256sumhash of the two separate files. - Compared the hashes provided to identify the differences.
Task 1. Generate hashes for files
The lab started in my home directory, /home/analyst, as the current working directory. This directory contained two files, file1.txt and file2.txt, which contained different data.
In this task, I displayed the contents of each of these files. I then generated a hash value for each file and sent the values to new files, which I used to examine the differences in these values later.
I used the ls command to list the contents of the directory. Two files, file1.txt and file2.txt, were listed. Then, I used the cat command to display the contents of the file1 and file2. That was the result:
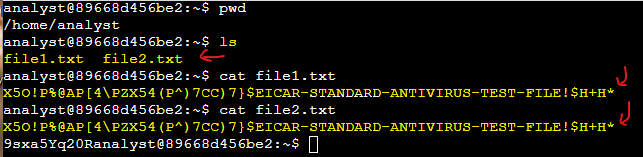
Although the contents of both files appeared identical when I used the cat command, I needed to generate the hash for each file to determine if the files were actually different.
I used the sha256sum command to generate the hash of the files:
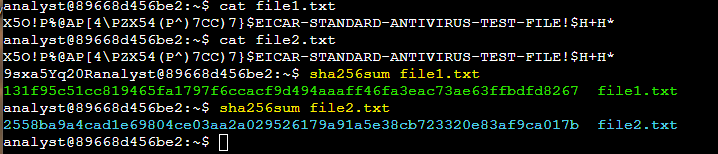
I noticed that the generated hash value for file1.txt was different from the generated hash value for file2.txt, indicating that the file contents were not identical.
Task 2. Compare hashes
In this task, I wrote the hashes to two separate files and then compared them to find the differences.
I used the sha256sum command to generate the hash of the file1.txt and file2.txt, and sent the output to a new file called file1hash and file2hash respectively.
Note: Although the content in file1.txt and file2.txt previously appeared identical, the hashes written to the file1hash and file2hash files were completely different.
Next, I used the cmp command to compare the two files byte by byte. If a difference was found, the command reported the byte and line number where the first difference occurred.
I used the cmp command to highlight the differences in the file1hash and file2hash files:
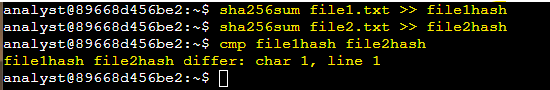
The output of the cmp command indicated that the hashes differed at the first character in the first line, indicating that the contents of the two files were different because the hash values of each file were different.
Conclusion
These are valuable tools I can use to validate data integrity as I contribute to the control of any organization’s security.
I practiced how to:
- Compute hashes using
sha256sum - Display hashes using the
catcommand - Compare hashes using the
cmpcommand