LetsDefend | SOC | SIEM Walkthrough - Phishing Alert - Deceptive Mail Detected
Introduction
In my journey to becoming a skilled SOC analyst, I aim to immerse myself in practical labs and real-world scenarios to prepare for the challenges of defending against cyber threats. The LetsDefend platform provides an incredible opportunity to simulate working in a Security Operations Center (SOC), enabling hands-on experience with investigating and responding to various security incidents.
This walkthrough showcases how I tackled a phishing alert using LetsDefend’s SOC environment, honing my cybersecurity skills in the process.
What is LetsDefend?
LetsDefend is a hands-on Blue Team training platform that simulates a SOC environment. It allows users to gain practical experience by investigating real-world cyber attack scenarios, working on alerts, and applying industry-standard processes to identify, contain, and remediate threats.
What is a SOC?
A Security Operations Center (SOC) is the command center for an organization’s cybersecurity defenses. SOC analysts monitor and analyze network activity, detect threats, and take action to protect the organization from cyber incidents. A SOC combines skilled personnel, advanced technologies, and robust processes to safeguard an organization’s assets and data.
What is Phishing?
Phishing is a cyber attack where threat actors use fraudulent communications—often via email—to deceive recipients into revealing sensitive information, such as login credentials or financial data. This type of attack remains one of the most common and effective methods used by cybercriminals.
Activity Overview
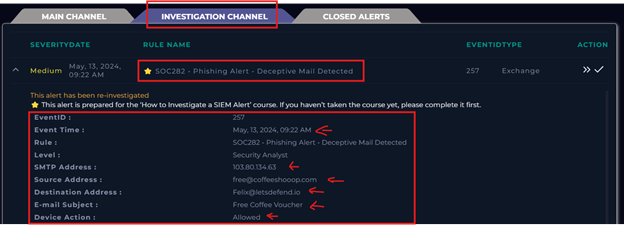
Event ID 257: SOC282 — Phishing Alert — Deceptive Mail Detected
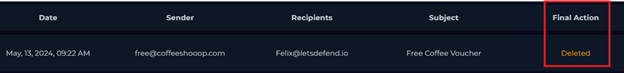
In this scenario, a suspicious email with the subject line “Free Coffee Voucher” was sent to a user named Felix on May 13, 2024,
at 9:22 AM. The sender’s email address was free@coffeeshoop.com, and this triggered the SOC282 rule: Phishing Alert -
Deceptive Mail Detected.
Despite being flagged as suspicious, the email security product marked the action as “allowed,” meaning no preventative measures were taken to block or quarantine the email.
The goal of this investigation was to analyze the alert, identify any malicious intent, and determine the necessary actions to protect the network from potential harm.
Steps Taken
1.Check the SOC Ticket Queue
2.Take Ownership and Create a Case
3.Utilize the Playbook
4.Email Analysis
5.Analyze URLs and Attachments
6.Containment and Remediation
7.Report Artifacts and IOCs
8.Close the Ticket
TASK 1 - Check the SOC Ticket Queue
The SOC ticket queue is essential for managing incidents effectively. It allows analysts to track, prioritize, and triage alerts while maintaining accountability and providing insights for trend analysis.
In LetsDefend’s SOC simulation, I accessed the ticket queue under the “Practice” tab and navigated to the “Monitoring” section to locate the phishing alert.
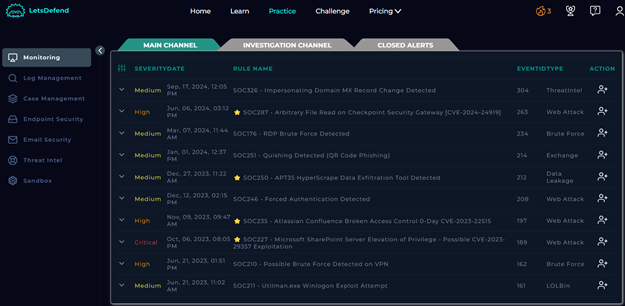
There, is possible to see all the generated SIEM alerts on the SOC queue, and filter by Severity level.
TASK 2 - Take Ownership and Create a Case
After identifying the phishing alert, I took ownership of the ticket by pressing the action button on the Main channel. The ticket now is seen on the Investigation Channel. There, I created a case to document my investigation and actions. Proper case management ensures the incident is tracked and resolved systematically.
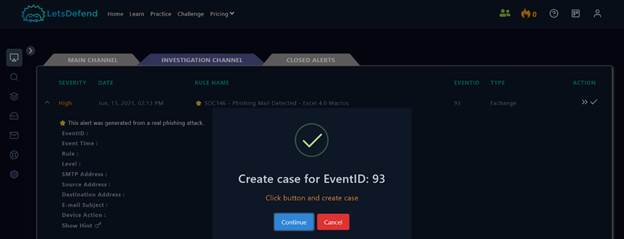
TASK 3 - Utilize the Playbook
Alerts can vary widely, from phishing to malware, web attacks, and ransomware. Each alert type requires a different approach for investigation and response. Playbooks provide structured workflows to ensure consistent and effective handling of alerts generated by SIEM or other security tools.
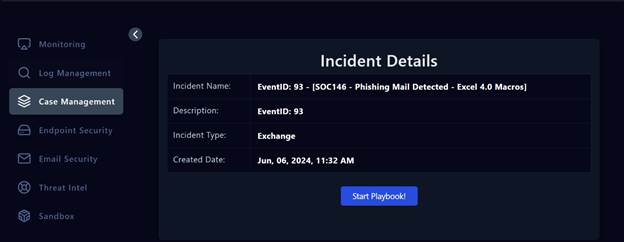
I followed the playbook provided by LetsDefend, which outlined standard operating procedures for analyzing and addressing phishing alerts.
TASK 4 - Email Analysis (from Playbook)
The first step of the playbook,'Parse Email', instructs us to gather key details about the received email, including information such as sender, recipient, time, and any suspicious content or attachments.
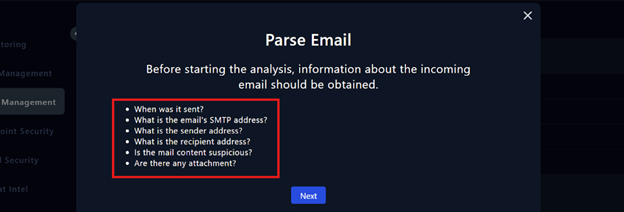
The initial analysis is critical and helps SOC teams quickly understand the threat, prioritize their response, and focus on the most critical issues to avoid wasting time and resources. This step sets the stage for an effective incident response.
I reviewed the email details,including headers and metadata, to confirm the suspicious nature of the message. Also, that there is an suspicious attached file!
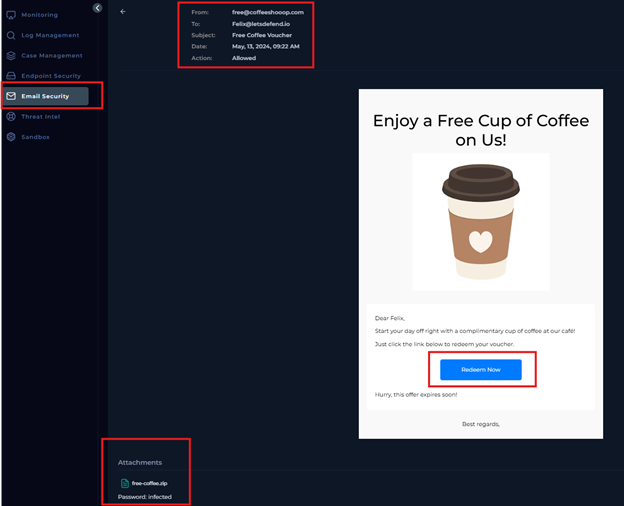
TASK 5 - Analyze URLs and Attachments (from Playbook)
When assessing emails, it is essential to examine any included URLs and attachments. Utilizing third-party sandbox environments enables safe analysis of these elements, ensuring we can detect potential threats without compromising system integrity.Key Objectives of URL and Attachment Analysis:
- Malware Detection: Attachments are frequently used to deliver malware such as viruses, ransomware, and trojans. By analyzing these files, we can proactively identify and block malicious content, preventing it from affecting the network.
- Phishing Detection: Malicious attachments are often part of phishing schemes aimed at stealing credentials or deploying harmful payloads. Through careful analysis, we can uncover these deceptive attempts and safeguard sensitive information.
The Playbook itself suggest tools for scan and check the suspicious URL’s. Also, LetsDefend provides a static and robust sandbox (offline) for defenders utilize.
Hint: Nice to use the following free services/products to investigate:
- AnyRun : An interactive malware analysis service, sandbox.
- VirusTotal : A service that analyzes files and URLs for viruses.
- URLHouse : A database of malicious URLs.
- URLScan : A tool for scanning and analyzing websites.
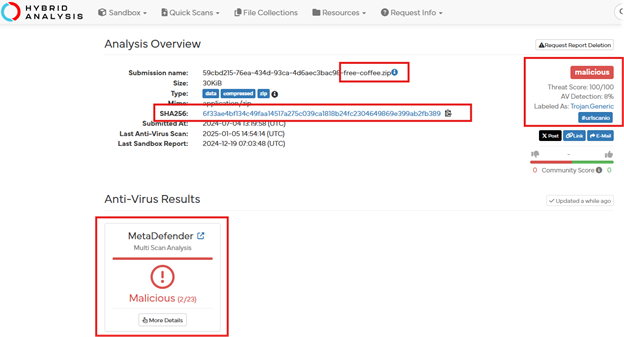
- HybridAnalysis : A free malware analysis service.
From the initial analysis, I could identify both attachments, and suspicious click button. Also, the SIEM alert shared the SMTP address associated with the suspicious email: SMTP IP: 103.80.134.63.
From the “copy link address” browser feature, I could obtain the
Malicious attachment url: https://files-ld.s3.us-east-2.amazonaws.com/59cbd215-76ea-434d-93ca-4d6aec3bac98-free-coffee.zip
Running these URL’s and IP’s on the specific tools, I could immediately presented with both concerning and useful information: the attachment has been flagged as malicious.
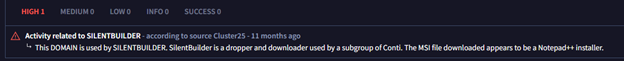
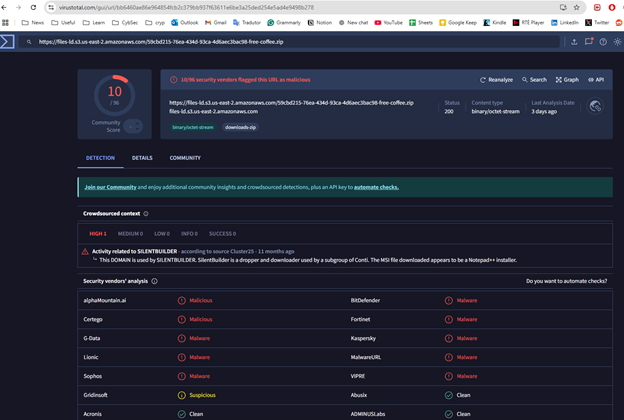
We can obtain precious information regarding the malicious file within these tools, as all the cybersecurity community works to keep them accurate. Also, these information will be used as notes/IOCs findings and reported and enrich the alert documentation and closure.
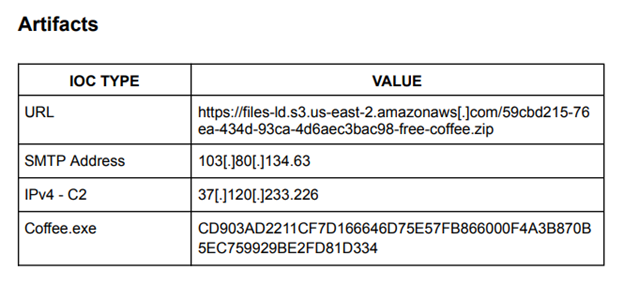
Artifacts founded until now:
- A string that may be used as part of an injection method.
- Queries process information.
- Contains the ability to terminate a process.
- Found a reference to a WMI query string known to be used for VM detection.
- Possibly checks for the presence of a forensics/monitoring tool.
- Contacts 1 host (37.120.233.226 | Port 3451/TCP | Origin: Romania).
- PID: 7508
- 6f33ae4bf134c49faa14517a275c039ca1818b24fc2304649869e399ab2fb389 | SHA256
- Associated URL: hxxps://files-ld.s3.us-east-2.amazonaws.com/59cbd215–76ea-434d-93ca-4d6aec3bac98-free-coffee.zip
- AsyncRAT| AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on GitHub as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions.
To avoid extensive detailing of this phase, I have demonstrated here only the query in VirusTotal and Hybrid Analysis, but I really suggest to any case/alert/file should be meticulous analyzed in a SAFE environment, as suggested on the Playbook and/or best practices.
In the next step of the playbook, we need to check if the mail was delivered to the user.
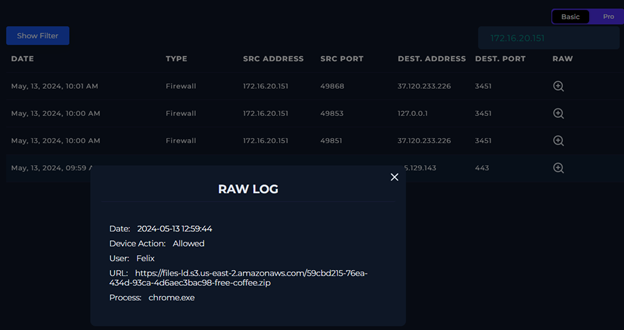
According to the device action section of the alert details, the email was permitted and successfully delivered to the user, Felix.
TASK 6 - Containment and Remediation (from playbook)
Upon confirming the phishing attempt, I took action to contain the threat by
alerting relevant stakeholders and blocking the identified URLs and sender
domain.
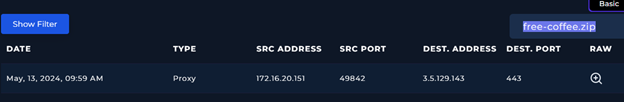
After that, I conduced a Network and Log analysis on the end point affected. Felix station, which IP address is: 172.16.20.151.
When filtered for the given Felix’s client IP address and also the malicious file “free-coffee.zip” I could see the traffic.:
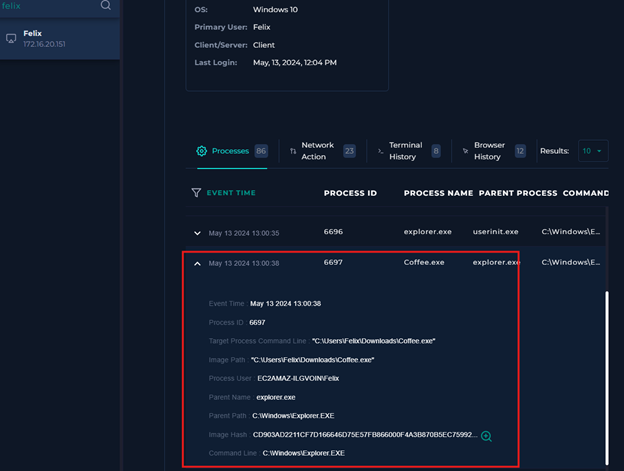
On the Felix terminal host, I could see in details what this file done:
Also, the Browser History and Network Action logs:
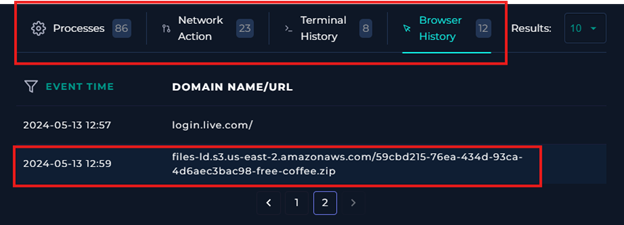
It is extremely important to check if the malicious agent or C2 (Command-and-Control) had contact with anyone else on the network, and avoid any unwanted surprise!
What is C2 ?
C2, or Command and Control, refers to the systems or infrastructure used by cyber attackers to remotely control compromised systems within a network. It is a critical component of many types of cyberattacks, particularly those involving malware, botnets, or advanced persistent threats (APTs).
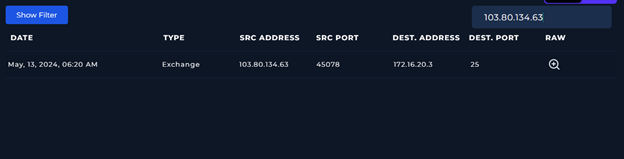
It is ok! From the Log Management view, we can see that No one else (except Felix) received that harmful email.
Remediation Actions
We have already removed the malicious email from the user's mailbox, but it is essential to educate the user on how to recognize and avoid phishing emails in the future to reduce the risk of similar incidents.
Remediation is a critical aspect of a comprehensive cybersecurity plan. It involves addressing vulnerabilities and security concerns to prevent exploitation, safeguard data, ensure operational continuity, and comply with regulations, ultimately strengthening the organization's security posture.
- Train employees on identifying and reporting suspicious emails, and provide guidance on avoiding phishing attacks.
- Reset any compromised credentials and enforce a strong password policy.
- Implement email filtering and security protocols, such as DKIM and SPF, to detect and block spoofed emails.
TASK 7 - Report Artifacts and IOCs (from playbook)
I documented all indicators of compromise (IOCs) and artifacts associated with the phishing email in the case file for future reference and threat
intelligence sharing.
The document should outline your rationale, relevant data or observations, and the actions taken during the investigation. This is essential as it creates a record of your analysis and can be referenced later or used to address similar alerts in the future.
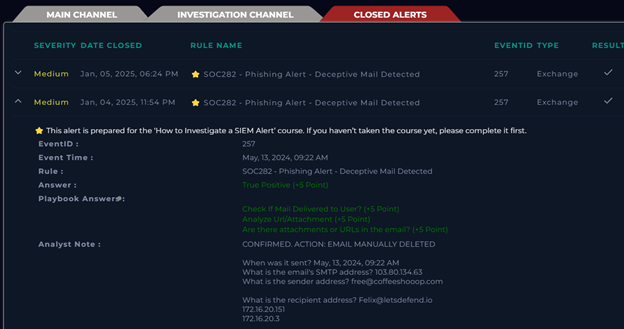
TASK 8 - Close the Ticket
The alert must be examined to determine whether it is a true positive or a false positive. A true positive indicates that the alert is valid and requires further action, while a false positive suggests that it is a false alarm.
After completing our investigation, we can confidently classify this alert as a True Positive.
Once the playbook is completed, and all steps, including the analysis phase, have been addressed, we must return to the Monitoring page within the Investigation channel to officially close the alert.
Conclusion
This exercise on LetsDefend provided me with hands-on experience in analyzing and responding to phishing alerts within a simulated SOC environment. By leveraging the tools, processes, and techniques available, I gained practical skills in incident management, email analysis, threat containment, and reporting—all essential capabilities for a SOC analyst.This experience underscores the importance of continuous learning and applying theoretical knowledge in practical settings to stay prepared for real-world cybersecurity challenges.