Let'sDefend - Malicious Document Analysis
As part of my ongoing journey in cybersecurity, I engaged in malicious document static analysis through the Let'sDefend SOC Career Path course. This hands-on activity involved identifying, analyzing, and interpreting malicious components embedded in a document, emphasizing the importance of proactive detection and mitigation in cybersecurity operations.
Overview
This activity focused on malware delivery via macros embedded in Microsoft Office documents, a common technique used by attackers to execute malicious payloads. By utilizing a combination of open-source and forensic tools, I gained proficiency in detecting and analyzing malicious document artifacts, including:
- Identifying malicious VBA macros and their execution methods.
- Extracting hidden content and metadata to uncover suspicious activity.
- Analyzing document behavior through hash verification and threat intelligence platforms like VirusTotal.
- Leveraging tools like ExifTool, strings, xorsearch, and Oletools for in-depth static and dynamic analysis.
Significance
The project demonstrated the real-world application of cybersecurity methodologies to combat evolving threats in document-based malware. It honed my ability to:
- Detect macro-based malware used for phishing campaigns and data exfiltration.
- Investigate malicious payloads and obfuscation techniques deployed by attackers.
- Provide actionable insights to mitigate document-based attacks, a critical skill in SOC and incident response roles.
Attackers' Use of Macros
Attackers have taken advantage of documents by using macros. Macros have been used by malicious actors to deliver malware.
Macros refer to scripts or small programs embedded within documents (such as Word, Excel, or PowerPoint files) that are written in VBA (Visual Basic for Applications). Macros are designed to automate repetitive tasks, like formatting data or generating reports, but attackers often exploit them for malicious purposes.
How Macros Are Used in Malicious Documents:
- Execution of Malicious Code:
- Attackers embed VBA scripts into documents that execute when the document is opened or specific actions (like enabling macros) are performed.
- These scripts can download and execute malware, steal data, or perform other harmful actions.
- Social Engineering:
- Users are tricked into enabling macros by enticing them with messages like: "This document contains protected content. Enable macros to view it."
- Once enabled, the macro executes the malicious payload.
- Common Attack Techniques:
- Downloading Malware: The macro connects to a remote server to download malware (e.g., ransomware, Trojans).
- Exfiltrating Data: The macro collects sensitive information and sends it to an attacker.
- Spawning Shells: Macros can be used to execute system commands or open a backdoor to give attackers control.
Static Malicious Document Analysis
File link: PO-465514-180820.doc.zip
Pass: infected
⚠️ BE CAREFUL, THIS IS A REAL MALWARE
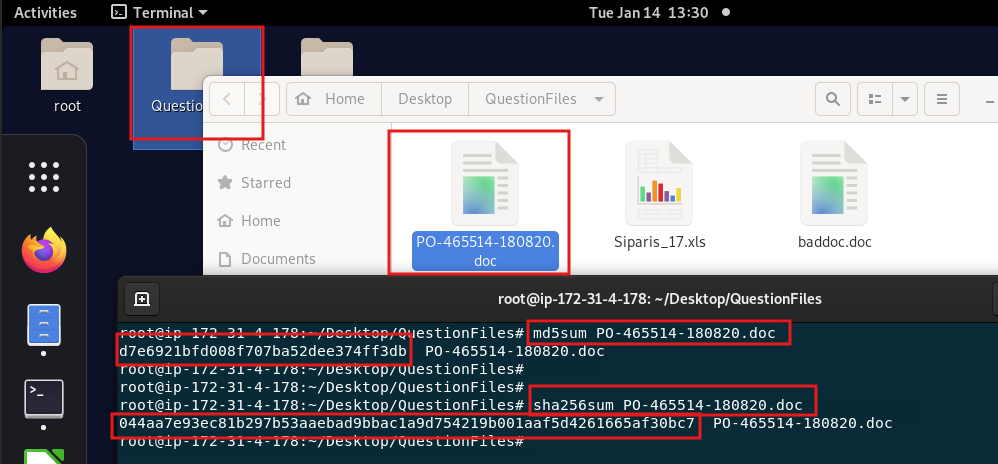
1 - Finding the MD5 value of the "/root/Desktop/QuestionFiles/PO-465514-180820.doc" file
- Open the file on terminal and type the command:
# md5sum “file name”
# sha256sum “file name”
2 - Checking the hash on the cyber community:
VirusTotal search: 50/62 flagged as malicious:
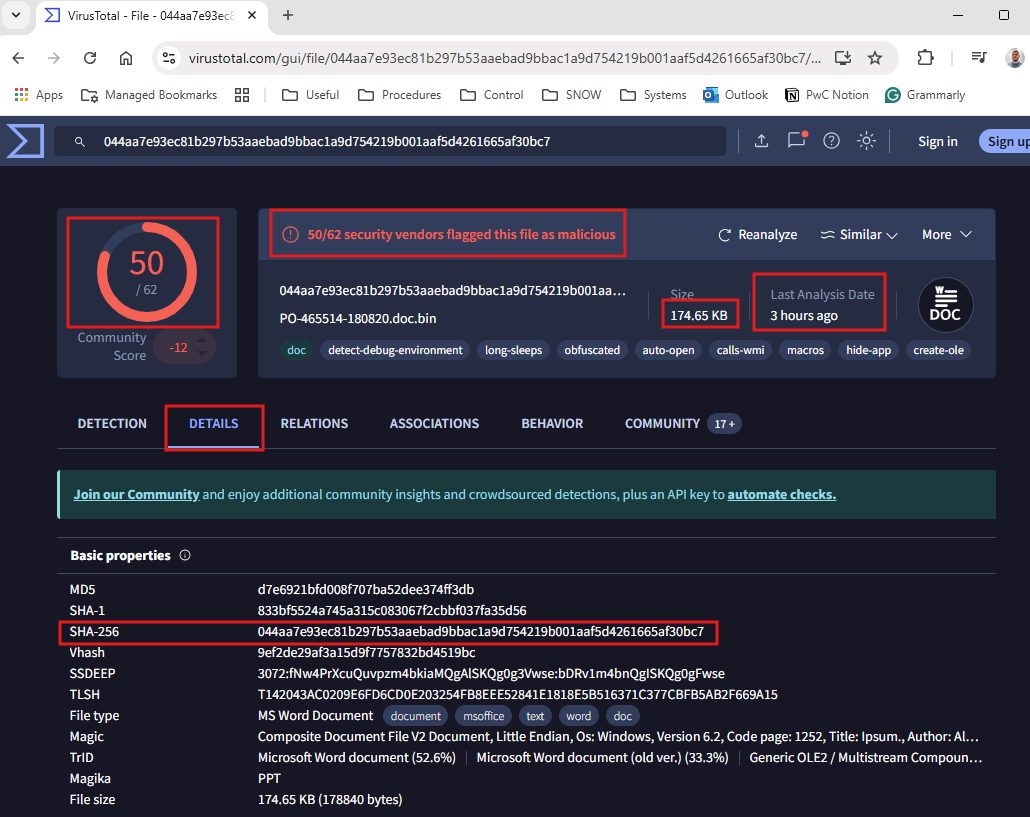
There are other information channels (mentioned below), but in order to reduce the size of the activity, I only kept VirusTotal. ALWAYS remember to get as many sources/info as possible!
- AnyRun
- VirusTotal
- URLHouse
- URLScan
- HybridAnalysis
3 - Next step, tool called exiftool
ExifTool is a command-line tool for reading, writing, and editing metadata in various file formats. It supports EXIF, IPTC, XMP, and other metadata standards. Useful for digital forensics and cybersecurity, it helps extract detailed file information, including creation dates and hidden data.. We should pay attention to any suspicious information like data creation/modification, type, language, template, size, etc:
# exiftool “File name”
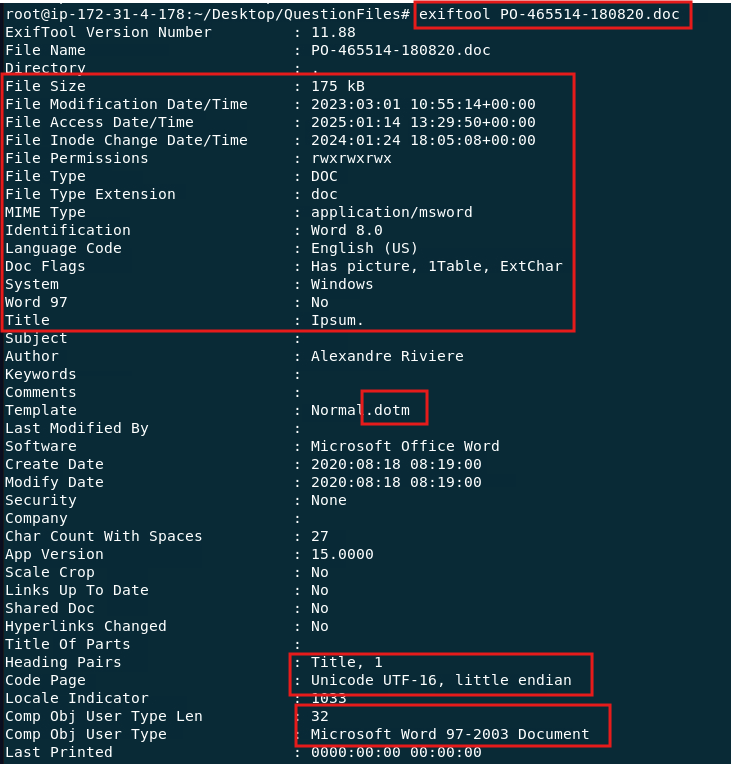
Details that caught my attention:
- Creation date 2020, modification date 2023 !?
- Template as file.dotm (m basically means macro, which is usually inserted as malicious repetitive tasks on files).
- File permissions: all ?!
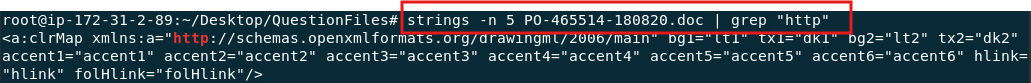
4 - Strings tool
The strings tool in Linux is used to extract printable ASCII or Unicode strings from binary files, which are often filled with unreadable or non-human-readable data. This tool is particularly useful for analyzing executables, documents, or other binary files to uncover potentially suspicious or embedded content.
Basic Usage of strings:
strings [options]
Example usage:
strings suspicious_file.exe
What to look for:
- IP Addresses
- Websites / Domains
- Suspicious File locations
- Malicious files, codes
5 - Xorsearch tool
Xorsearch is a powerful tool for analyzing binary files to identify and extract hidden data, particularly obfuscated or encoded strings.
Key Features of xorsearch:
- XOR Encoding Detection
- Custom Pattern Matching
- Supports Multiple Encoding Methods
- Extract Hidden Data
Installing xorsearch:
- Clone the Repository:
- Navigate to the Folder:
- Run xorsearch:
git clone
cd DidierStevensSuite
xorsearch [options]
6 - Oletools
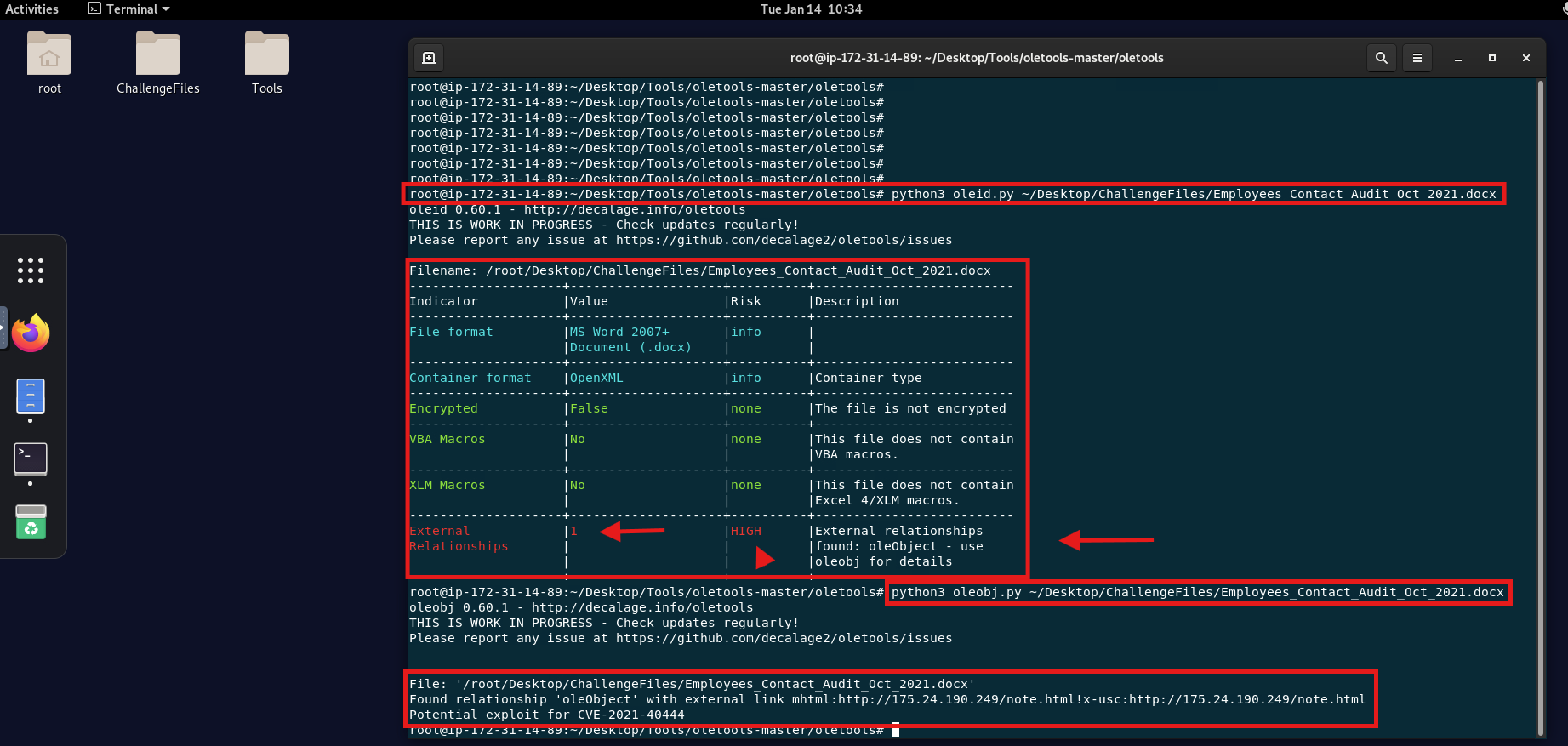
Oletools is a collection of Python tools to analyze Microsoft Office files (e.g., .doc, .xls, .ppt), OpenXML formats (.docx, .xlsx), and other files containing embedded OLE (Object Linking and Embedding) objects.
Key Tools in Oletools:
- oleid: Scans OLE and OpenXML files for common signs of malicious behavior.
- olevba: Extracts and analyzes VBA (Visual Basic for Applications) macros embedded in Office documents.
- olemeta: Extracts metadata from OLE or OpenXML documents.
Conclusion
Analyzing malicious documents is a vital skill for cybersecurity professionals, as attackers often exploit macros and document features to deliver malware or steal sensitive information. Tools like hash-checking utilities, ExifTool, and strings help identify anomalies such as suspicious metadata, embedded macros, and obfuscated content. Techniques such as hash verification and extracting readable strings provide critical insights into the document's behavior and potential threats.
Advanced tools like xorsearch and Oletools further enhance analysis by decoding obfuscation and identifying malicious VBA scripts or embedded objects. This comprehensive approach ensures that threats are identified effectively, enabling faster incident response and proactive risk mitigation. By mastering these tools and techniques, professionals can stay ahead of attackers and strengthen cybersecurity defenses.